 WIPO’s release of its latest version of ePCT, with its two new user-friendly approaches to two-factor authentication, provides some perspective. Against this perspective, conspicuous by its absence is any hint or suggestion of USPTO moving to some user-friendly approach to two-factor authentication.
WIPO’s release of its latest version of ePCT, with its two new user-friendly approaches to two-factor authentication, provides some perspective. Against this perspective, conspicuous by its absence is any hint or suggestion of USPTO moving to some user-friendly approach to two-factor authentication.
A moment’s review of the USPTO situation follows. Some twelve years ago the USPTO launched EFS-Web and Private PAIR. The login mechanism was a two-factor authentication system. By this we mean that a would-be wrongdoer who hoped to sneak into Private PAIR would have to (a) somehow know your password and (b) somehow be in possession of your USPTO cryptographic certificate. The idea was that hopefully a would-be wrongdoer would rarely if ever satisfy both of these conditions.
USPTO’s way of doing this was astonishingly poorly designed and equally poorly implemented. USPTO outsourced this design to a company called Entrust. Entrust’s design was a “java applet” system in which the user’s web browser was required to permit a computer program to run in an execution space connected with the web browser. The computer program was written in the java programming language. As it turns out, this web browser execution space approach was a grave security risk. It was easy to devise java programs which, when executed in this browser execution space, would infect the computer with a virus or wreak other havoc upon the computer.
Laid on top of this risk-prone “java applet” approach was a further problem. The system designed by Entrust for distributing and managi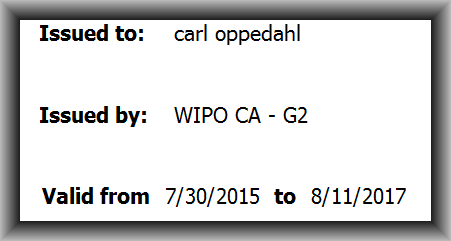 ng cryptographic certificates was itself astonishingly poorly designed. A given user’s cryptographic certificate might expire without warning at any time. It was then, and is now, impossible for a user to even check to learn when his or her USPTO certificate was going to expire. Was it scheduled to expire in a week? In a month? In a year? Impossible to know.
ng cryptographic certificates was itself astonishingly poorly designed. A given user’s cryptographic certificate might expire without warning at any time. It was then, and is now, impossible for a user to even check to learn when his or her USPTO certificate was going to expire. Was it scheduled to expire in a week? In a month? In a year? Impossible to know.
In contrast the system designed by WIPO permits the user to learn, with just a few mouse clicks, exactly when his or her WIPO crypto certificate will expire. See above.
In recent years the various browser designers had made no secret of their plans to block java applets completely. See my blog article about this.
In recent years many people, including me, urged the USPTO to dump its crypto certificate infrastructure (with its hidden and unpredictable expiration dates). And in recent years, many people, including me (blog article), urged the USPTO to scrap the Java applet approach to two-factor authentication.
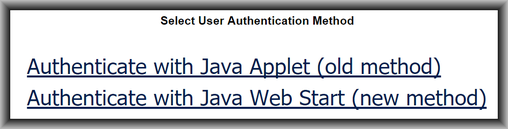
Eventually the various browser designers followed through on their stated plans to block java applets that run within the browser. One might have hoped that USPTO would respond by migrating to some new two-factor authentication mechanism. This did not, however, happen. USPTO stubbornly clung to its user-unfriendly crypto certificate infrastructure (with its hidden and unpredictable expiration dates). And USPTO went back to Entrust and adopted an awkward Entrust-designed java applet workaround. In this workaround, the java applet does not run inside the browser but instead runs in an execution space outside of the browser. This outside-the-browser execution space is provided by the operating system rather than being provided by the browser. A malevolent designer of java applets would need to find some security flaw in the operating system itself to make progress in breaking into the user’s computer. The main risk-shift here is simply that if something bad happens with a java applet that is running in an execution space that is outside of the browser itself, then the browser publisher cannot be blamed for whatever happens.
So that’s the background. Then the recent events. The recent events are that WIPO has released a new version of ePCT. And this new version of ePCT offers the user the choice of several different two-factor authentication mechanisms. Indeed the system allows the user to set up multiple mechanisms. So the user could on Monday use a browser cryptographic certificate as the second factor (the first factor being a password). On Tuesday the user could use an SMS (text message) as the second factor. On Wednesday the user could use Google Authenticator as the second factor of a two-factor authentication. I wrote about this here.
So why, why, why is it that after years of being urged to do so, USPTO has still not adopted any of the user-friendly two-factor approaches that others have adopted?
Anyway, WIPO’s having released a system that lets the user pick his or her preferred method of two-factor authentication ought to serve as yet another example to the USPTO how to do things better.
What’s refreshing is not only that WIPO’s system lets the user pick his or her preferred method of two-factor authentication. WIPO’s system also lets the user activate as many as three different methods of two-factor authentication.
One wishes that USPTO could take WIPO’s example and offer several approaches for two-factor authentication.

One Reply to “Why can’t USPTO use a user-friendly two-factor authentication?”