Here is how things are looking on the denial-of-service attack (previous blog article) on VOIP.MS, my favorite VOIP service provider.
It has now been something like nine days that somebody has been attacking the Canadian company that my firm has been using for all of our telephone services for the past four years or so. I have felt, and continue to feel, that the people running the company are as smart as the people running any VOIP service provider, and smarter than most.
Again by way of background what we are talking about generally is companies that provide completely unbundled telephone services. There is a mechanism called DID which is how incoming calls from the public switched telephone network can reach your phones or your PBX. There is a mechanism by which your phones can place outbound telephone calls. These and other related services all pass over the Internet.
Most of the customer-facing providers of unbundled VOIP service will have one or two servers, located perhaps on the East Coast of the US and the West Coast. One of the striking things about VOIP.MS is that they have always had many, many servers at more than a dozen locations around the US as well as servers outside the US. This means that a customer of VOIP.MS can choose to route its calls through a server that is geographically nearby to the customer’s phones or users.
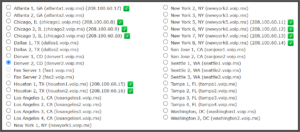
The latest word from VOIP.MS is that they are in a process of deploying “improved security” on certain of their servers. They indicate this with a green check mark on their server list. What you see above is what I found today on their server list for the US. Up until now my firm had been routing most of our telephone services through a server in a very large windowless building in the Denver Tech Center (the server denoted “denver2” in the server list above). That server does not have a green check mark.
The experiment that I will try next is to migrate some of our telephones and ATAs over to chicago3. This is in a tall building in the west “loop” of downtown Chicago that was once a printing plant and is now a server farm. I picked that server because it has a green check mark and because it is the next nearest location (as compared to Denver) to some of our people and equipment locations.
One might be tempted to worry about things like latency or propagation delay, picking a server that is perhaps a thousand miles away from a phone or an ATA. But one must recall that most well-known providers of unbundled VOIP servers only have one or two servers at all, maybe only one on the East Coast and one on the West Coast.
A remaining judgment call is whether to reprogram the affected telephones and ATAs using the IP address 208.100.60.10 or using the fully qualified domain name (FQDN) chicago3.voip.ms. Because the people of our firm are all pretty tech-savvy, and know how to do things like logging in at the administrative interface of their phones to do configuration updates, I will start by having them make use of the IP address. Later once the attack is a thing of the past and stuff has settled, we will return to the use of FQDNs.

Is the building you referred to in Chicago the Steadfast DC at 725 S Wells? I think that is the Empire Paper building. It’s only 8 stories with a basement.
Yes. See https://blog.oppedahl.com/?page_id=4081 .
Hmmm. “[T]all, building” and “west ‘loop'” were great distractors because I couldn’t think of a building that had those characteristics and also is now a data center and was once a printing plant. For a moment I thought you might be thinking of 10 S Canal, which is a famous AT&T/Illinois Bell CO complex. I think it’s 27 stories, which might be “tall” even in Chicago, and it’s in the West Loop, which Empire Paper is not. But it was purpose-built for the phone company, not a reclaimed printing plant.
I think Steadfast also has some space in the former R.R. Donnelley/Lakeside Press/Calumet building, where Sears catalogs once were printed, and which has been turned into a data center and carrier hotel. It’s much larger–more than a million square feet.