
The USPTO did a bad thing the other day. It told its customers, falsely, that the only way to do time-based one-time passwords is to use Oracle’s app. USPTO says “you must have the Oracle Mobile Authenticator app on your mobile device” to do one-time passwords. This is flatly false and it wrongly favors a particular company. Hopefully the USPTO will remedy its mistake immediately. I’ll explain this.
By now in 2017, everybody knows what two-factor authentication is, and everybody knows how to do two-factor authentication. The idea is that instead of just using a password to log in, you use two factors (hence the term “two-factor authentication”). There are clunky ways to do this, such as sending you a text message on your cell phone or sending you an email with a Secret Code Number in it. There is a supremely clunky way to do this, namely the Entrust Java Applet which USPTO unwisely selected a decade ago as the way to log in at Private PAIR and EFS-Web. (See my May 2014 blog article entitled “A reminder that USPTO needs to scrap the Entrust java applet for PAIR and EFS-Web“.)
But in addition to the clunky ways to do two-factor authentication, there are smart ways to do it. Some years ago the IETF (the computer nerds who figure out smart ways to make the Internet better) standardized what is now known as the TOTP algorithm. TOTP is an open and published standard for generating a six-digit code that changes every sixty seconds, for use in logging in along with your password.
Smart system administrators use TOTP. WIPO started using it in its ePCT system about a year ago. When I log in to my blogging server to post blog articles like this, I use TOTP to log in.
There are many, many apps which you can use for TOTP.

The best known TOTP app is Google Authenticator (round gray logo at right). My personal favorite these days is Winauth (cinquefoil blue logo at right). And yes, you can use Oracle’s Mobile Authenticator app if you wish.
And yes, you can use Oracle’s Mobile Authenticator app if you wish.
But it is simply false to say (as USPTO says) that the only way to do TOTP is by means of Oracle’s Mobile Authenticator app.
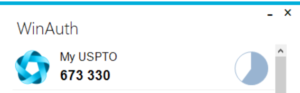 When I log in at MyUSPTO using two-factor authentication, I use WinAuth. Here you can see the six-digit code that I used a few minutes ago to log in at MyUSPTO. This is living proof of the falsity of USPTO’s assertion that the only way to do TOTP on MyUSPTO is by means of the Oracle Mobile Authenticator.
When I log in at MyUSPTO using two-factor authentication, I use WinAuth. Here you can see the six-digit code that I used a few minutes ago to log in at MyUSPTO. This is living proof of the falsity of USPTO’s assertion that the only way to do TOTP on MyUSPTO is by means of the Oracle Mobile Authenticator.
WIPO got it right when it launched its TOTP functionality a year ago, as you can see in WIPO’s FAQ about TOTP in ePCT. WIPO avoided endorsing just one provider of a TOTP app but instead named more than one provider and disclosed that there are many such providers.
What is particularly unfortunate about USPTO’s endorsement of Oracle’s app (and failure to mention that there are many other such apps) is that it overshadows what could have been a good-news story about the USPTO. The good-news story could have been USPTO’s having finally taken a small step toward adopting a well-designed two-factor authentication system (TOTP), a step which would eventually permit USPTO to scrap the very poorly designed Entrust Java applet system.
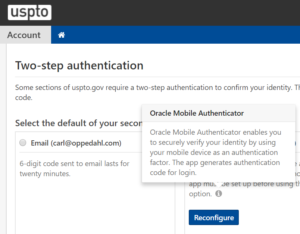 USPTO’s explicit endorsement of Oracle’s app (see another example at right), and failure to mention that there are many providers of apps which support this open standard, should never have happened but is easily remedied.
USPTO’s explicit endorsement of Oracle’s app (see another example at right), and failure to mention that there are many providers of apps which support this open standard, should never have happened but is easily remedied.

I tried to set up WinAuth and couldn’t get it to configure. USPTO asked for 2 codes and WinAuth only gives one. Could you please provide a bit more instruction on how to set it up? Thanks
Yes the problem is at the USPTO, not with WinAuth. You would have the same problem even if you use the app that USPTO says is the only one that works (Oracle). The USPTO instructions for setting up the TOTP connection are inadequate.
Basically you click around to the page at USPTO that asks for the two codes. Then you go and look at the app and memorize one of the codes. Then you key in that code at USPTO. Then you go back to the app and by then probably 30 seconds have passed. Now there is a new and different code on the screen of the app. So you memorize that second code. And you go back to USPTO and key in the second code. Now you have keyed in two codes — a first code and a second code. Then you click “submit” or whatever. And then you are all set.
Thanks! That worked.
You are correct as always, though perhaps slightly unsympathetic. I assume that the USPTO has a long list of tasks, and validating other auth apps for 2FA did not rise to the top. So they chose one (Oracle’s) for validation. Surprisingly enough, it’s one I didn’t realize existed.
At the moment, I can’t set up any 2FA app with the USPTO since on the screen where the 2FA QR code is supposed to be displayed, I get a salmon-colored error: “Message.There was an error with the system, please try again later.”
Perhaps in response to your post, the USPTO has now added a (not terribly prominent) note below the text asking you to install the Oracle app:
“Note: Other free authenticator apps may also work and will be officially supported in the future.”