 (Please also see a followup blog article here.)
(Please also see a followup blog article here.)
Those who make use of Private PAIR and EFS-Web are accustomed to USPTO’s very clunky way of accomplishing two-factor authentication, namely the poorly designed Entrust Java Applet (EJA). USPTO has now formally announced (see excerpt at right from a slide in a USPTO webinar yesterday) that it will replace EJA with a much more user-friendly approach. The goals of today’s blog article are:
- describe the new system, and
- explain what you can do right now to be ready for it well in advance.
First a reminder why it will be a great relief when EJA gets scrapped:
- It is impossible for the user to know in advance when exactly his or her EJA crypto certificate is going to expire. So it is impossible to plan ahead for the update.
- When EJA updates a user’s crypto certificate (which EJA does abruptly and without warning), EJA only updates one copy of the certificate. The many other copies that the user (and the user’s co-workers) have stored in various locations do not get updated by EJA. EJA does not tell the user which copy got updated, and so the user must then go on a treasure hunt to try to find the updated certificate.
- When things go wrong with EJA for a particular user, the assistance by the EBC requires that the EBC be open (and EBC is not always open) and sometimes takes days to carry out.
- USPTO refuses to issue an EJA crypto certificate to a person who is not a registered practitioner before the patent office. In an office with paralegals and assistants, this means there is no choice but for everyone to be given copies of one practitioner’s EJA crypto cert and for everyone to be given the EJA password.
- EJA relies upon a browser feature that exposes the user to security risks. The major makers of browsers have one by one eliminated that feature or have said they plan to eliminate it. This means that users have to migrate from one browser to the next to preserve their ability to log in to Private PAIR and EFS-Web. Eventually there won’t be any browser left that will permit the use of EJA.
I have blogged about the need to scrap EJA here in 2014 and here in 2015 and here in 2017. Now in 2018, USPTO plans to scrap EJA. USPTO presented a webinar yesterday (slides here) in which this topic was discussed.
The new system. The USPTO’s new system uses TOTP. TOTP is an open-source, non-proprietary published algorithm designed by the very smart people in the IETF. The idea of TOTP is that you install an app on your smart phone or on your notebook computer. When the time comes to log in on a USPTO system, you type in your user ID and password. Then (this is the important part) the USPTO web page asks for a Secret Code Number. You open the app on your phone, and click the app to display your Secret Code Number. You then type that number into the USPTO web page. And now you have logged in using two factors, namely “something you have” (the Secret Code Number) and “something you know” (your password).
Importantly, the Secret Code Number changes every sixty seconds. This means that even if someone were to learn the particular Secret Code Number that you used to log in, they would not be able to make any use of that particular Secret Code Number at a later time.
Many readers will already have such an app on their smart phone, for example to do two-factor logins for computer banking or at the WIPO ePCT system. My app provides Secret Code Numbers so that I can two-factor logins for many systems, including the USPTO system, and Google, and Amazon, and Stripe (the credit card processor that our firm uses), and the admin interface for the WordPress system that hosts this very blog.

The best known TOTP app is Google Authenticator (round gray logo at right). My personal favorite these days is Winauth (cinquefoil blue logo at right).
When I log in at MyUSPTO using two-factor authentication, I use WinAuth. 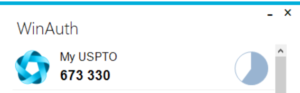 Here you can see the six-digit code that I used recently to log in at My USPTO.
Here you can see the six-digit code that I used recently to log in at My USPTO.
What you can do right now to get ready. Now we get to the important part of today’s blog article. If you want to be trendy, modern, and up-to-date, you will do several things now to be ready for this transition that USPTO will carry out in “late 2018”.
First, hopefully you already have a user ID and password in USPTO’s MyUSPTO system. These days basically “MyUSPTO” is the same thing as the Financial Manager system, but eventually “MyUSPTO” will expand to cover Private PAIR and EFS-Web. Anyway, if you do not already have a user ID and password in USPTO’s MyUSPTO system, now (today!) is the time to get the user ID and password. This is quite easy. With a few mouse clicks, the MyUSPTO system sends you an email. You click on a link in the email and you are done. You have a user ID and password.
Second, having already gotten yourself a user ID and password in the MyUSPTO system, get a TOTP app. If you want to get a compliment from your IT person, go see him or her and ask them which TOTP app they recommend. They will be delighted that you even asked this question and they will be glad to expound at some length about the advantages and disadvantages of the various TOTP apps. They might settle upon Authy or Google Authenticator or Winauth or maybe their favorite is a different one. Post a comment below about the recommendation that you received from your IT person!
Or maybe you already have a TOTP app on your smart phone or notebook computer. If so, good for you for being trendy, modern, and up-to-date!
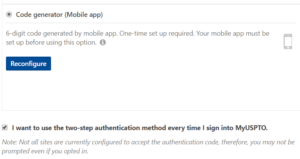
Third, synchronize your TOTP app with the MyUSPTO system. To do this, click around in the “my account” section of My USPTO and find the section for “two-step authentication” (see screen shots at right). Click the button for “Code generator (Mobile app)” and follow the steps to synchronize the MyUSPTO system with your app.
Fourth, get together with all of the people in your office who are presently sharing somebody’s EJA crypto certificate and password. Importantly, each of these people needs to follow the three steps just mentioned. Each of these people needs to obtain their own personal user ID and password in the MyUSPTO system. Each of these people needs to get a TOTP app on their smart phone or computer if they have not already done so. And each of these people needs to synchronize their TOTP app with the MyUSPTO system.

Having done all of these things, you and your co-workers will be very well positioned for the transition that will happen in “late 2018”. When USPTO makes the change so that you must migrate from the EJA to the New Authentication Method, you will be ready for it. Quoted at right is slide 35 from yesterday’s USPTO slide presentation. You can see where it says “Users can prepare now by creating their MyUSPTO accounts”. I have highlighted this in green. Yes, as this slide from the USPTO recommends, users should prepare now by creating their own MyUSPTO accounts. (And they should set up TOTP for their MyUSPTO accounts.)
Many good things will flow from your efforts.
As a first example, maybe you have been dragging your feet when you were repeatedly nudged by Amazon or Google or your bank that it would be a good idea to implement TOTP for your logins. If you start getting familiar with a TOTP app because of your efforts with MyUSPTO, this will get you accustomed to the spiffy TOTP app that you will have installed on your smart phone or notebook computer. You will then be able to turn on two-factor authentication for your bank, and you will greatly reduce the risk of a bad person hacking your computer banking and cleaning out your bank account.
As a second example, likely as not you will be at a cocktail party next week or next month, and somebody will mention that they have heard they need to install a TOTP app on their smart phone. And you can pull your smart phone out of your pocket protector and show them your TOTP app and you can explain how it works. (Okay maybe not every reader of this blog carries their smart phone in a pocket protector.) But even if you don’t use a pocket protector, you will earn geek points from everyone within earshot at the cocktail party, and you will get invited to more cocktail parties in the future due to your enhanced geek status.
As a third example, imagine that you might be in some conversation with a client who mentions casually that they are implementing TOTP in their latest consumer product or their latest software-as-a-service. And you can casually ask which app they prefer for TOTP. Then you and the client can compare the aesthetics and functionality of this TOTP app and that TOTP app, and you will have gained some geek stature in the mind of your client.
A fourth important reason for you to do this TOTP stuff in MyUSPTO is to send a subtle but potent signal to the USPTO that they are doing the right thing by making these baby steps toward scrapping the EJA. Every month some project manager at the USPTO (I think I know who it is!) will get a report on their desk that adds up how many users have implemented TOTP in their MyUSPTO account. Right now I suspect the number is very small, fewer than ten. But hopefully the readers of this blog will all invest the five or ten minutes, and the fifteen or so mouse clicks, required to carry out the three steps mentioned above. And hopefully the readers of this blog will coordinate with their co-workers to carry out the fourth step mentioned above. And hopefully the monthly TOTP report on this person’s desk will show a bigger number next month and a still bigger number the month after that.
To reinforce this point, consider that there are surely some decisionmakers at USPTO who dread the scrapping of the EJA, since the transition away from EJA will inevitably lead to a deluge of frantic telephone calls to the EBC from people who suddenly discover they cannot log in to Private PAIR and EFS-Web any more. If more people get TOTP configured now, if the numbers in the monthly report get bigger, then hopefully this dread can be reduced at least a little.

This will be a great change.
Any word on the automatic timeout system? Seems too short to me. Sometimes step out to grab coffee and come back to see I am automatically logged out of the USPTO system.
They said eMOD automatic timeout will be after 30 minutes of inactivity.
The USPTO will also implement email as a two-factor authentication method, seemingly an alternative to the TOTP approach.
Sounds great, but my attempts with two different authenticator apps failed to repeatedly, throwing the message “Could not validate authentication codes. Contact UCC (USPTO Contact Center). Toll-Free: 800-786-9199.” However, that number is a general purpose number. Eventually I got a person, who gave me their actual number, which is 2025752000, and their division in the USPTO, which is IMTAS. (I now await a call back.) RICK NEIFELD
I had the same problem. I tried both the Oracle authenticator the PTO claims to support and the Google one.
This is the very first TOTP implementation that has requested two codes for validation. The other 9 TOTP logins I have requested only one.
I wonder if this implementation difference is causing your problem. For me, Duo Mobile worked fine.
Yes I noticed this design mistake by the USPTO as well. Nobody who is implementing TOTP needs two codes to synch the devices. It is a bad design mistake that USPTO is requiring two codes to synch the devices.
I had the same issue but I kept trying and it eventually worked.
This is fantastic! I just synchronized my TOTP app with my MyUSPTO system. It was very quick and easy to do. I have always used Google Authenticator, but I am interested to know why WinAuth is your personal favorite.
Carl,
I agree with your take on most things, and the current EPF system is well out of date. However, I think you might be too harsh on the original architects. The USPTO 2FA predates any other 2FA system I have used by many years and, at the time, in-browser Java was widespread.
Thankfully, the USPTO has rolled out the Java Web Start (new method) so we can log into Private PAIR using, for example, Chrome. That has resolved the browser compatibility issues and the security issues attendant to enabling in-browser Java. I know you’re well aware of the new method, so this portion of the comment is more for others’ benefit.
So I’m still unsure how the delegate thing is going to work. My paralegal sets up an account and enables TOTP for their account how does that allow them to file on my behalf when I have my own account w/ enabled TOTP?
I don’t know that the USPTO people who are designing this new login mechanism have figured it out yet.
Clearly there will have to be some overlay of roles and permissions and handshakes to define who is allowed to do what.
Hopefully USPTO will be smart and will alpha-test the overlay rather than designing it and baking it into the databases and only then testing it with real users after irrevocable design decisions have been locked in.
Hopefully they will invite you to be among the alpha testers.
USPTO’s track record in this area is very, very poor. The yucky Entrust java applet login scheme got irrevocably folded into the system before anybody outside of the USPTO was permitted to beta test. Worse, the approach where the only way for a paralegal to assist a practitioner is for the two to share an account and password is an approach that got designed in before any real-life practitioners were permitted to beta test.
But maybe the leopard will change its spots, so to speak. Maybe this time the USPTO people will get folks like you and me involved early enough that if the proposed permissions overlay is a disaster, it will be possible to scrap it and try again.
Many thanks, Carl!
Requesting the TOTP authentication method when I tried to set up the account kept failing. I had to select two-step verification by email first and then, after getting the account running, switch to the TOTP authenticator in the Account settings. I tried both the Oracle and Google apps and settled on the Oracle one as suggested by the USPTO website.
Works great.
Carl, What would we do without you ? Thanks for everything you do for patent professionals!
Finally did this! It worked very well. Thanks, Carl!