
Starting just now, WIPO has made it possible to use two new authentication mechanisms for ePCT, in addition to the one authentication mechanism that has been available in the past. In this article I mention things that you might want to think about in picking an authentication mechanism to use.
What we are all accustomed to is the cryptographic certificate mechanism for access to ePCT. For many years, the ePCT user has been in the position of needing to obtain a cryptographic certificate from WIPO, installing the certificate in one’s web browser, and uploading the public-key portion of the certificate to the ePCT system. In this way, a person logging in to ePCT is doing a particular type of “two-factor authentication”. The user is identified to ePCT by means of (1) one’s password and (2) one’s cryptographic certificate which is stored in one’s web browser.
The crypto certificate mechanism works. It successfully provides one of the two factors for the purposes of “two-factor authentication”.
Today’s news is that WIPO has just now released a new version of the ePCT system which permits a user to set up two additional mechanisms for two-factor authentication. I will describe these two mechanisms and I will offer some thoughts about how you might pick as between the various mechanisms.
Before we get to deeply into this somewhat complicated subject, let me skip ahead to the answer. The answer is that every reader should simply do what it takes to set up both of the new additional mechanisms for two-factor authentication. Just do it. There is no drawback to doing it. The only possible affect of doing it is to save you some trouble or fuss in the future. Just do it.
The two newly available authentication mechanisms are Google Authenticator and SMS text messaging.
 To use Google Authenticator (“GA”), you download the GA app onto your smart phone. (Or if you are sufficiently trendy you had already downloaded and installed the GA app onto your smart phone for authenticating other systems.) You can see the icon for GA at the top of this blog article. You then click around within ePCT to find the place where you add GA. It displays a bar code on the screen. You click the “plus” button in GA to add a new system. You then snap a picture of the bar code. GA then displays a six-digit secret code number. You key the number in at ePCT. And you’re all done.
To use Google Authenticator (“GA”), you download the GA app onto your smart phone. (Or if you are sufficiently trendy you had already downloaded and installed the GA app onto your smart phone for authenticating other systems.) You can see the icon for GA at the top of this blog article. You then click around within ePCT to find the place where you add GA. It displays a bar code on the screen. You click the “plus” button in GA to add a new system. You then snap a picture of the bar code. GA then displays a six-digit secret code number. You key the number in at ePCT. And you’re all done.
Having done this, for future logins, you will have the option of doing two-factor authentication where one factor is your password and the other factor is the secret code number from GA.
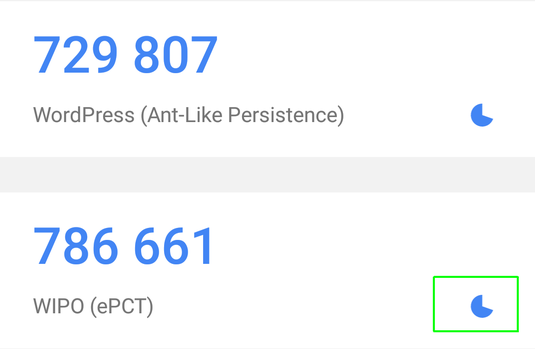
The screen shot above shows part of my GA display. You can see the secret code number for me to log in to this blog. And you can see the secret code number for the ePCT system.
The point of GA of course is that the secret code number changes every sixty seconds. So it does not compromise the security of this blog, or the security of the PCT applications in my ePCT account, to publish the secret code numbers here.
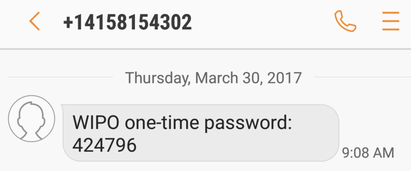 The next one is the SMS (short message service) mechanism, namely a text message sent to your cell phone. To set this up, you click around within ePCT to find the place where you add SMS. You type in your phone number. (Do it international style, starting with the plus sign and the country code.) The ePCT system sends you a text message containing a six-digit secret code number. (An example of an SMS containing such a secret code number appears above.) Your phone displays the secret code number. You key the number in at ePCT. And you’re all done.
The next one is the SMS (short message service) mechanism, namely a text message sent to your cell phone. To set this up, you click around within ePCT to find the place where you add SMS. You type in your phone number. (Do it international style, starting with the plus sign and the country code.) The ePCT system sends you a text message containing a six-digit secret code number. (An example of an SMS containing such a secret code number appears above.) Your phone displays the secret code number. You key the number in at ePCT. And you’re all done.
Having done this, for future logins, you will have the option of doing two-factor authentication where one factor is your password and the other factor is the secret code number from a text message.
The point here is to do both. Add both mechanisms to your ePCT user account. That way, if you ever have trouble using any one of the authentication mechanisms (crypto certificate, Google Authenticator, text message) you can switch to a different mechanism.
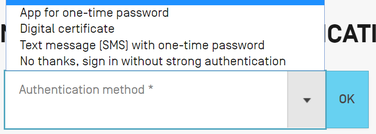 How to pick? How should you pick among these mechanisms? Once you have set up the various mechanisms, then at login time ePCT will show a drop-down menu like this at right.
How to pick? How should you pick among these mechanisms? Once you have set up the various mechanisms, then at login time ePCT will show a drop-down menu like this at right.
One of the choices is “no thanks”. If you pick this choice, then you will find yourself in the “public ePCT” system, namely the part of the system that is sort of like Public PAIR.
Crypto certificate. If you already have a crypto certificate, and if it is already installed in your web browser, and if you have already uploaded the public key of the certificate to ePCT, and if the certificate has not yet expired … then you might as well use this mechanism. For the time being.
But some time you will be using a browser that is on somebody else’s computer. And you will want to log in at ePCT. And the crypto certificate won’t already be inside that browser. And then you will be very glad that you already set up GA and SMS.
Or your computer will crash or get stolen and you will be setting up a new computer. And you won’t already have the crypto certificate handy. In which case you will be very glad that you already set up GA and SMS.
And eventually your crypto certificate will expire. I just looked in the certificate manager of my browser, and I see that my WIPO crypto certificate will expire in August of 2017. When the expiration happens to you, you will be glad that you already set up GA and SMS.
For a new user of ePCT, if you have not already gone through all of the steps for setting up a crypto certificate, you may simply want to skip all of that and go directly to the GA and SMS authentication mechanisms.
SMS. The ePCT system also supports SMS. There are, I suppose, some advantages to the SMS mechanism. One thing is that you don’t have to install an app on your phone. You simply use the text messaging capability that is already in your phone.
A drawback to the SMS approach is that it costs money. Or it might cost money, depending on your carrier service plan. A more serious problem with SMS is that you might be located in the bowels of some building where there is no cell coverage. Or you might be on an airplane or in a train at a location where there is no cell coverage.
A further drawback to the SMS approach is that it is so … two decades ago. No self-respecting geek or techy person would be caught dead using SMS to communicate with anybody else. The modern way to send and receive text messages is via Whatsapp (blog article) or less secure systems like Wechat or Line or Skype.
Google authenticator. The trendy, modern and up-to-date way to go is Google Authenticator. If you are in a meeting with a high-tech client, and you pull out your phone and open up GA, and read the six-digit secret code number, and key it in to ePCT… then what will stick in the client’s mind is that you are smart about protecting client secrets.
Now let’s see who wins a prize. The winner of the prize will be the first reader to post a comment explaining the function of the symbol within the green rectangle.

The symbol in the green box is a timer showing how much longer the one-time password is valid in Google Authenticator.
The symbol is the Google App Authenticator where you scan the barcode and then it will give you a one-time password!
Expiration timer for the code.
Bruce beat me to it. I took too long to read.
The symbol is pac-man wearing blue. Actually it is the amount of time left before the time for the six digit code runs out.
I thouight the USPTO was shutting down the “old method.” Your article seems to suggest otherwise. Is the “new method” necessary?
This is about WIPO’s ePCT system, NOT the USPTO’s EFS-Web.
Is anyone having an issue with the digital certificate method of authenticating and after authenticating it opens a web page that simply says “page cannot be displayed”? We’ve checked the cert expiration and it is still valid. We use IE 11 and can see the cert installed in the browser. I had ePCT support look at it a verify settings were correct. Perhaps there’s something they missed? Any advice will be rewarded with [imaginary] diamonds! Thanks!
If you have not already done so, I recommend you explore the other two kinds of secure authentication. The one-time-password app approach, and the SMS message approach.