The question presented (and answered) here is “which GL.iNet routers provide VLAN wifi client isolation?”
By way of background, one of the richest product lines for home and small-office Internet routers is that of GL.iNet. Four particular reasons to select GL.iNet instead of any of dozens of other brand names (for example TP-Link, Linksys or Netgear) are:
-
- the GL.iNet routers are much less expensive,
- the GL.iNet routers run open-source firmware, so you don’t need to wonder whether somebody has programmed a back door into the software of the router,
- the GL.iNet routers provide fast and easy-to-use clients and servers for OpenVPN and Wireguard (blog article on Wireguard servers), and
- the GL.iNet travel routers make it easy (with just a few mouse clicks) to connect to an existing wifi network in a hotel or public place and to provide your own wired-ethernet connections and your own wifi network (blog article).
The big-brand Internet routers, for example TP-Link, Linksys or Netgear, all come out of the box with proprietary firmware. You have no choice but to wonder, what if somebody has programmed a back door into the router. They cost more money than the GL.iNet routers.
Of course if you care about the security benefits of running open-source firmware on your home or small-office Internet router, one path is to “grow your own”. You can take just about any brand of Internet router and erase its firmware and load your own open-source firmware onto it. (The two most popular bodies of open-source Internet router firmware are OpenWRT and Tomato.)
Which brings us to the natural question, what about GL.iNet routers and VLANs? What about setting up one’s home or small office network using a GL.iNet router so that the (relatively untrusted) IOT (internet of things) devices are relegated to a VLAN that is separate from the trusted VLAN for one’s personal computer and file server? (See my blog article Setting up a VLAN for your IOT devices for an introduction to this topic.) In this blog article, I observed that there is no consistency of terminology across various manufacturers for VLAN configurations.
This natural question can be fleshed out into a wish list:
-
- It would be nice to have a VLAN to which (relatively untrusted) IOT devices could be relegated;
- it would be nice if the wifi devices on the untrusted VLAN were isolated from each other;
- it would be nice if all of this could be accomplished with an off-the-shelf Internet router (not requiring such dramatic steps as erasing the firmware and installing new firmware);
- it would be nice if all of this could be accomplished with mere mouse clicks (not requiring hard-to-learn and fiddly ssh shell command line configuration steps);
- it would be nice if this could be done with a router that does not use proprietary firmware (meaning the router uses open-source firmware);
- it would be nice if the router could be less expensive than most other-branded routers
- it would be nice if the router runs at gigabit speed or faster for its LAN and WAN ports;
- it would be nice if the wifi on the router operates using wifi 6, meaning an overall wifi bandwidth of up to about 1800 megabits per second;
- it would be nice if the wifi on the router offers MIMO with at least two MIMO channels and maybe four or even six MIMO channels.
For many users, it would also be nice if the router offered simple easy-to-use fast VPN server functions such as Wireguard.
The alert reader will have no difficulty guessing where I am going with all of this. Surely what I am going to say next is “use a GL.iNet router”. And indeed that is approximately what I am going to say next. The challenge, however, lies in the italicized wish-list item above: isolating the untrusted IOT wifi devices from each other.
As it turns out, the ability of the OpenWRT firmware to accomplish isolation of untrusted IOT wifi devices from each other is dependent upon the particular hardware (the particular processor) upon which the OpenWRT firmware has been installed. I have just now personally tested eight models of GL.iNet router and I report the results here.
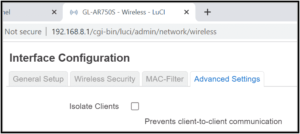
The way that you find out whether a given GL.iNet router provides isolation of untrusted IOT wifi devices from each other is … you power up the router, and you click around in the “advanced” interface which is called LuCI (documentation page), and then you click on “network” and then “wireless”. And then you look to see if “advanced settings” is available. If it is, then the “isolate clients” check box is visible, and this means the router is able to isolate clients. An example of a good-news screen shot appears at right.
I have confirmed through actual testing that GL.iNet routers that support isolation of untrusted wifi clients include the following:
Here are two GL.iNet routers that do not support isolation of untrusted wifi clients:
| model number | model name | processor | image |
| MT1300 | Beryl | MediaTek MT7621 @880MHz |
 |
| MT300N-V2 | Mango | MediaTek MT7628NN @580Mhz |
 |
My guess is that every GL.iNet router that starts with “MT” fails to provide isolation of untrusted wifi clients. My guess is that every GL.iNet router that starts with “A” or “SFT” does provide isolation of untrusted wifi clients.






