This blog post describes a Patentcenter feature request — a direct link from any particular patent application file to a page for e-filing in that particular patent application. Continue reading “Patentcenter feature request: direct link from application file to e-file in that application”
PCT-SAFE — one more step towards oblivion

One of the reasons why filers need to start learning to use ePCT (if they have not done so already) is that some day PCT-SAFE will be gone. Yesterday, PCT-SAFE took one more step towards oblivion. Continue reading “PCT-SAFE — one more step towards oblivion”
Patentcenter ticket tracking
Those who regularly use EFS-Web and Private PAIR need to be joining the beta-testers of Patentcenter. You need to do this because eventually USPTO will shut down EFS-Web and Private PAIR. You need to find the bugs in Patentcenter and you need to figure out what features need to be requested in Patentcenter. To this end you should probably join the Patentcenter listserv. And to this end I have set up two very simple pages:
- a Patentcenter trouble tickets page, and
- a Patentcenter feature requests page.
If you find a bug in Patentcenter that you think needs to be listed on the trouble tickets page, join the listserv and bring it up there. Members of the listserv can then add it to the trouble ticket page. Similarly if you think of a feature that needs to be added to Patentcenter, bring it up in the listserv and we can then add it to the feature requests page.
Patentcenter web-based Form 85B is broken three ways

(Update May 12, 2020: now it is broken only two ways. The initial cap for the city name has been fixed.)
USPTO will eventually shut down EFS-Web and the only patent e-filing system available to applicants will be Patentcenter. So it behooves all of us to take the present opportunity to beta-test Patentcenter as fully as we can, to try to get USPTO to fix its defects and to try to get USPTO to make it user-friendly. (Probably this means you should join the Patentcenter listserv.) Here is a defect that I keep running into in Patentcenter, namely that the web-based Form 85B drops the initial capitalization for the city name for the assignee. I reported this to the USPTO a year ago and it has still not been fixed. But there are two other ways that this feature of Patentcenter is broken. Continue reading “Patentcenter web-based Form 85B is broken three ways”
Patentcenter Corrected ADS is broken in at least three ways
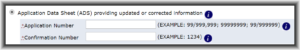
(Update. The developers quietly removed this feature from Patentcenter on about May 10. See blog article.)
One of the features of EFS-Web is the web-based Corrected ADS (quoted at right). You enter an application number and confirmation number and EFS-Web will construct for you a Corrected ADS with strikethroughs and underscores compliant with 37 CFR § 1.76.
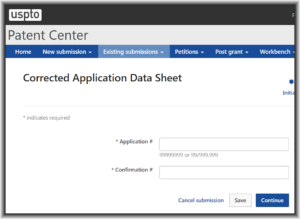
Patentcenter has a corresponding function (quoted at right). But this Patentcenter function is broken — it loses things and does not tell you that it lost them. (There are also two other broken things about the Patentcenter Corrected ADS function as I will discuss below.) Until USPTO fixes the software, you need to be extremely cautious if you decide to try using the Corrected ADS function in Patentcenter. I will discuss it now in more detail, with some background from EFS-Web as well. Continue reading “Patentcenter Corrected ADS is broken in at least three ways”
What does EALNRO mean?
Yes, what does EALNRO mean? It means “expressly abandoned leaving no rights outstanding”. And why is that phrase important? Continue reading “What does EALNRO mean?”
“Send email” button still missing from Patentcenter
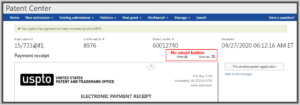
Users of EFS-Web are accustomed to the notion that any time we e-file anything, once we have finished we can click a button to send an email. In my office the routine is that the filer clicks the button to send an email message to the docket desk so that they know what got e-filed.
The alpha testing of Patentcenter began in autumn of 2018. From the beginning of Patentcenter, there were some e-filing paths that would finish with no email button. There were only a few of us alpha testers and we all brought this up to the USPTO. There really needed to be an email button!
There are some e-filing paths in Patentcenter that do lead to a place where the user can click a “send email” button. But even now in 2020 there are e-filing paths in Patentcenter that lead to a place where the “send email” button is conspicuously absent.
One of USPTO’s stated design goals is “if you can do it in EFS-Web we will make it so that you can do it in Patentcenter”. This goal has not been met for the “send email” button. One hopes that eventually USPTO will get Patentcenter fixed so that there is a “send email” button every time the filer has successfully e-filed anything.
(Another of USPTO’s stated design goals is “if you can do it in Private PAIR we will make it so that you can do it in Patentcenter”.)
Is it a problem for you that some of the e-filing paths in Patentcenter finish with no “send email” button? Please post a comment below. (This is ticket number CP6.)
Supplemental Content missing in Patentcenter (corrected by USPTO on a Sunday)
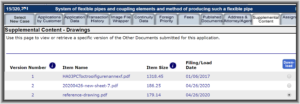
(Update: See update at the end of the blog article.)
There’s a very important database at the USPTO called Supplemental Content or SCORE. If you look up any particular patent application in PAIR or in Patentcenter, what gets listed for SCORE for that patent application should be absolutely identical. But strikingly often, they are not at all identical.
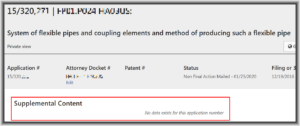
For example here is a case that has three drawings files in SCORE according to PAIR, but according to Patentcenter this same case supposedly has nothing in SCORE.
SCORE is very important. This is where your high quality drawings end up in your design patent applications. This is where your sequence listings end up.
I have dropped an email to ebc@uspto.gov with the application number, asking EBC to please open a ticket to get this fixed so that Patentcenter will show my SCORE files.
Have you checked all of your cases that have SCORE content? Do they show your SCORE content in Patentcenter? If not, you might want to get in touch with the EBC to get it fixed. And please post a comment below.
Update: I posted this on a Sunday, yesterday. The missing Score material included two files that I e-filed yesterday, as well as a file that had been in the case from more than a year earlier. The screen shot above shows that the file from more than a year ago was missing in Score in Patentcenter as of yesterday. About two hours after I posted this blog article, without any explanation from the USPTO, the Score file from a year ago suddenly for the first time became visible in Patencenter, along with the new newly e-filed files.
How many utility applications have been filed in Patentcenter thus far?
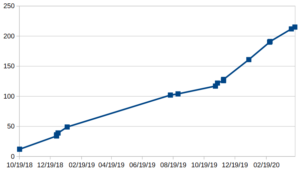
It looks as though it is possible to figure out how many utility patent applications have been filed in Patentcenter thus far during alpha testing and beta testing. Continue reading “How many utility applications have been filed in Patentcenter thus far?”
Patentcenter reel and frame number coding error solved by beta users
(Updated May 12, 2020. USPTO has fixed this bug, thus clearing trouble ticket CP8.)
Until this week the Patentcenter system was in a controlled beta test, accessible to only a very limited number of beta testers. This week USPTO made the choice to open the beta testing to everybody. This week I also launched the Patentcenter listserv, an email discussion group for users of Patentcenter. (To find out more or to subscribe, click here.) Listserv members have already solved a coding error that USPTO made in Patentcenter in the display of reel and frame numbers.
The way this started was that alert listserv member Shannon Vieau noticed that if you look at a reel and frame number for a patent application in PAIR, and if you look at the same patent application in Patentcenter, the reel and frame numbers don’t match. Prompted by Shannon’s posting, I looked up a few of my own applications, and they all likewise failed to match. I picked one that was a published case. For that case, the frame number is the same in the two places — 366. But in PAIR the reel number is 048299 while in Patentcenter the reel number is 17237. I posted the actual reel and frame numbers in this blog article.
At this point alert listserv member Richard Schafer wrote:
Guess what you get if you add 17237 to 48299: 65536. That just can’t be a coincidence. I haven’t checked any of my cases, but I’ll bet they’re all like that, suggesting some weird piece of bad handling of a 16-bit integer value. How that could pass any level of testing of the code, I can’t imagine.
65536 is one of those really interesting numbers for a person who does a lot of computer programming. It is 216.
Richard then looked up some of his own cases in PAIR and in Patentcenter, and here was his report:
I just confirmed my suspicion with two of my applications. The Patent Center reel number and the PAIR reel number always add up to 65536. That’s just hilariously broken.
At this point alert listserv member and experienced computer programmer Neil Ormos identified how USPTO can fix this coding mistake:
What a great catch! Someone at the PTO owes you a bug bounty!
That kind of error is fairly common. Someone writes the field as an unsigned int and then reads it back as a signed int, or uses sprintf(“%d”) when they should have used sprintf(“%u”). Happens all the time.
“Beta” testing is great, no? You just harness the customer as free labor, and they stand in line to volunteer!
So anyway the coding fix has now been posted here. It will be interesting to see how many days it takes USPTO to correct the coding error in Patentcenter. (This is trouble ticket number CP8, cleared May 12, 2020.)
