I have been seeing a bit of a trend lately. The trend is free wifi that is bla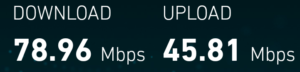 zing fast, many tens of megabits per second both up and down.
zing fast, many tens of megabits per second both up and down.
At right is a speed test result for the free wifi in the Wisconsin state capitol in Madison, Wisconsin. And this did not even require me to accept some terms and conditions.
Some time ago a friend was in the new Whitney museum in Manhattan. Again blazing fast, eighty megs down and fifty megs up. And again no need to accept terms and conditions.
It’s nice when this happens.
What’s the fastest free wifi you have encountered? Please post a comment.
The last time I tried to use the public wifi at the USPTO, which was a few months ago, the login process was so cumbersome that eventually I gave up and used my own wifi hotspot instead. The last time I did successfully log in to the public wifi at the USPTO, which was a few months before that, it was embarrassingly slow, slower than 100K bits per second up or down. Basically voice phone modem speeds.
Can someone who has recently made use of the public wifi at the USPTO share a comment about how fast the wifi was, and how easy or difficult the login process was?